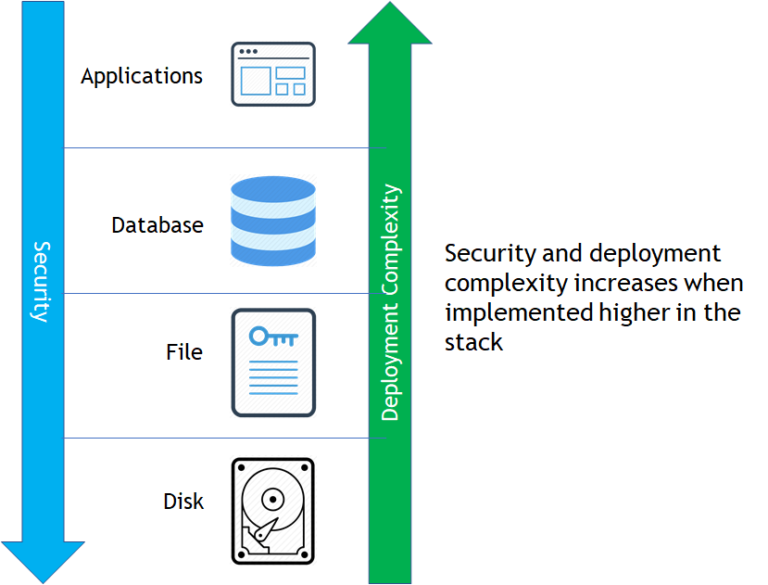
| FDE (Full-disk encryption) OR SED(Self-encrypting drives) | Simplest method of deploying encryptionTransparent to applications, databases, and users.High-performance, hardware-based encryption | Addresses a very limited set of threats—protects only from physical loss of storage media.Lacks safeguards against advanced persistent threats (APTs), malicious insiders, or external attackersMeets minimal compliance requirementsDoesn’t offer granular access audit logs | Mainstream cloud providers offer the functional equivalent of FDE with its attendant limitations listed aboveFDE makes sense for laptops, which are highly susceptible to loss or theft. But FDE isn’t suitable for the most common risks faced in data center and cloud environments |
| FLE (File-Level Encryption) | Transparent to users and applications, meaning organizations don’t have to customize applications or change associated business processesSupports both structured and unstructured dataEstablishes strong controls that guard against abuse by privileged users and that meet common compliance requirementsOffers granular file access logs and SIEM integration that can be used for security intelligence and compliance reporting | Encryption agents are specific to operating systems, so it is important to ensure the solution selected offers coverage of a broad set of Windows, Linux, and Unix platforms | For many organizations and purposes, file encryption represents the optimal approach. Its broad protections support the vast majority of use cases, and it is easy to deploy and operate. |
| DB Encryption OR TED (Transparent Data Encryption) | Safeguards data in databases, which are critical repositories.Establishes strong safeguards against a range of threats, including malicious insiders—even in some cases a malicious database administrator. | Offerings from one database vendor can’t be applied to databases from other vendors.Doesn’t enable central administration across multiple vendor databases or other areas in environment.Only encrypts columns or tables of a database, leaving configuration files, system logs, and reports exposed. | While database encryption technologies can meet specific, tactical requirements, they don’t enable organizations to address security across heterogeneous environments. As a result, they can leave organizations with significant security gaps. |
| App Encrytion | Secures specific subsets of data, such as fields in a database.Encryption and decryption occur at the application layer, which means data can be encrypted before it is transmitted and stored.Offers highest level of security, providing protections against malicious DBAs and SQL-injection attacks.Tokenization can also significantly reduce PCI DSS compliance costs and administrative overhead. | These approaches need to be integrated with the application, and therefore require development effort and resources. | These approaches may be optimal in cases in which security policies or compliance mandates require specific sets of data to be secured. In addition, variants of application-layer encryption, including tokenization and format-preserving encryption, can help reduce the impact on databases.Look for solutions with well-documented, standards-based APIs and sample code to simplify application developmen |